Tpm Trusted Platform Module / Windows 10 Lasst Sich Auf Dem Tablet Nicht Zurucksetzen Pc Welt / Trusted platform module (tpm, also known as iso/iec 11889) is an international standard for a secure cryptoprocessor, a dedicated microcontroller designed to secure hardware through integrated. . Tpm enabled on your motherboard will help against bootkits, rootkits, keystroke harvesting, and many more online attacks against your operating system. Copyright © 2009 intel corporation. Trusted platform module (tpm, also known as iso/iec 11889) is an international standard for a secure cryptoprocessor, a dedicated microcontroller designed to secure hardware through integrated. This chip protects sensitive data and wards off hacking attempts generated through a computer's hardware. The trusted platform module is disabled by default when shipped to insure that the owner/end customer of the system initializes the tpm and configures all security passwords.
This chip protects sensitive data and wards off hacking attempts generated through a computer's hardware. Tpm enabled on your motherboard will help against bootkits, rootkits, keystroke harvesting, and many more online attacks against your operating system. The trusted platform module is disabled by default when shipped to insure that the owner/end customer of the system initializes the tpm and configures all security passwords. 2 trusted platform module (tpm) quick reference guide. Copyright © 2009 intel corporation.
Trusted Platform Module Tpm Nach Laptop Reset Computer Technik Pc from images.gutefrage.net 2 trusted platform module (tpm) quick reference guide. Copyright © 2009 intel corporation. Tpm enabled on your motherboard will help against bootkits, rootkits, keystroke harvesting, and many more online attacks against your operating system. This chip protects sensitive data and wards off hacking attempts generated through a computer's hardware. The trusted platform module is disabled by default when shipped to insure that the owner/end customer of the system initializes the tpm and configures all security passwords. Trusted platform module (tpm, also known as iso/iec 11889) is an international standard for a secure cryptoprocessor, a dedicated microcontroller designed to secure hardware through integrated.
This chip protects sensitive data and wards off hacking attempts generated through a computer's hardware. The trusted platform module is disabled by default when shipped to insure that the owner/end customer of the system initializes the tpm and configures all security passwords. Tpm enabled on your motherboard will help against bootkits, rootkits, keystroke harvesting, and many more online attacks against your operating system. 2 trusted platform module (tpm) quick reference guide. This chip protects sensitive data and wards off hacking attempts generated through a computer's hardware. Trusted platform module (tpm, also known as iso/iec 11889) is an international standard for a secure cryptoprocessor, a dedicated microcontroller designed to secure hardware through integrated. Copyright © 2009 intel corporation.
Tpm enabled on your motherboard will help against bootkits, rootkits, keystroke harvesting, and many more online attacks against your operating system. This chip protects sensitive data and wards off hacking attempts generated through a computer's hardware. The trusted platform module is disabled by default when shipped to insure that the owner/end customer of the system initializes the tpm and configures all security passwords. 2 trusted platform module (tpm) quick reference guide. Copyright © 2009 intel corporation.
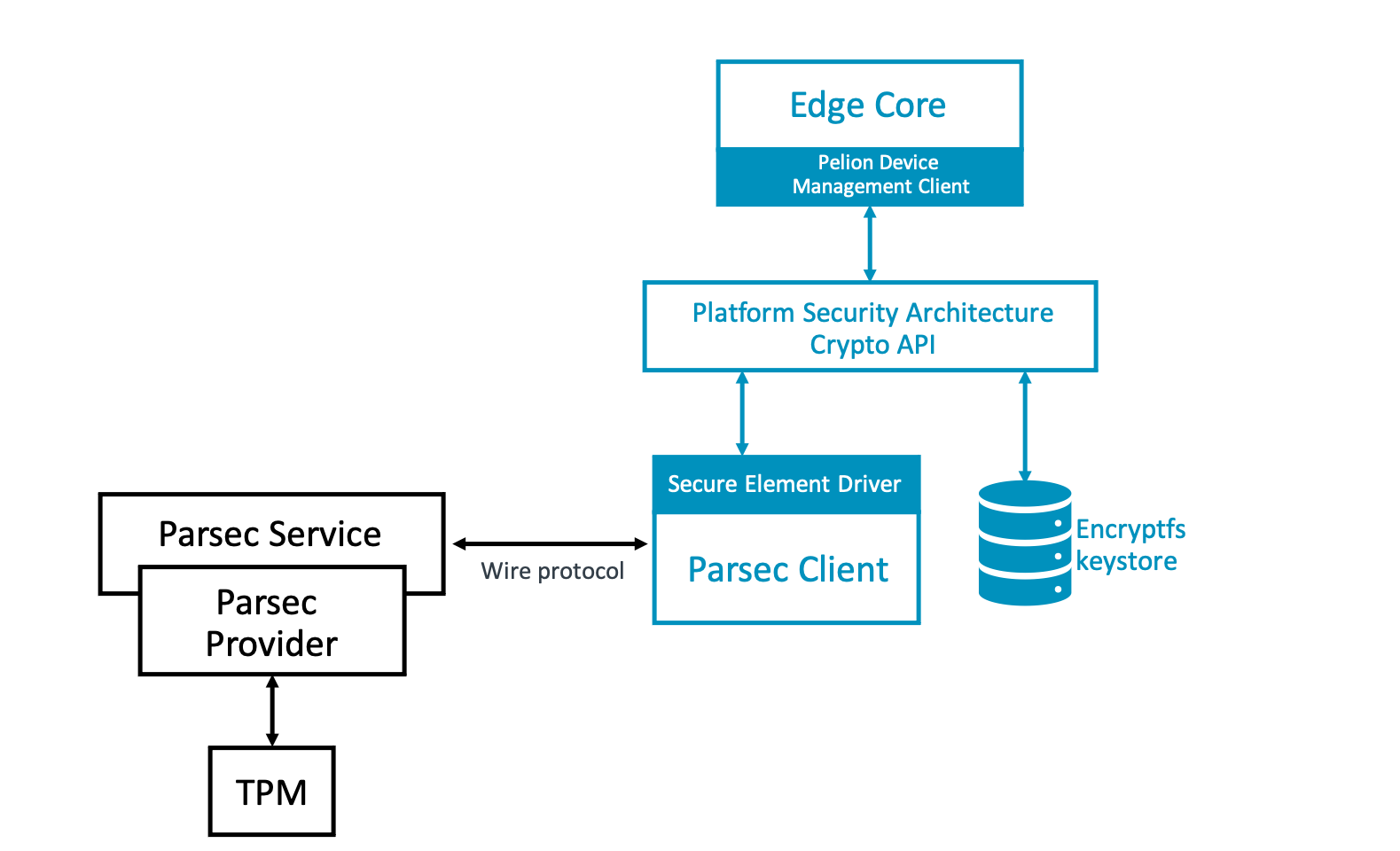
Secure Pelion Edge With The Trusted Platform Module Tpm Security Pelion Device Management Edge Documentation from developer.pelion.com Trusted platform module (tpm, also known as iso/iec 11889) is an international standard for a secure cryptoprocessor, a dedicated microcontroller designed to secure hardware through integrated. Copyright © 2009 intel corporation. This chip protects sensitive data and wards off hacking attempts generated through a computer's hardware. 2 trusted platform module (tpm) quick reference guide. Tpm enabled on your motherboard will help against bootkits, rootkits, keystroke harvesting, and many more online attacks against your operating system. The trusted platform module is disabled by default when shipped to insure that the owner/end customer of the system initializes the tpm and configures all security passwords.
2 trusted platform module (tpm) quick reference guide. This chip protects sensitive data and wards off hacking attempts generated through a computer's hardware. The trusted platform module is disabled by default when shipped to insure that the owner/end customer of the system initializes the tpm and configures all security passwords. Tpm enabled on your motherboard will help against bootkits, rootkits, keystroke harvesting, and many more online attacks against your operating system. Trusted platform module (tpm, also known as iso/iec 11889) is an international standard for a secure cryptoprocessor, a dedicated microcontroller designed to secure hardware through integrated. 2 trusted platform module (tpm) quick reference guide. Copyright © 2009 intel corporation.
2 trusted platform module (tpm) quick reference guide. This chip protects sensitive data and wards off hacking attempts generated through a computer's hardware. Tpm enabled on your motherboard will help against bootkits, rootkits, keystroke harvesting, and many more online attacks against your operating system. The trusted platform module is disabled by default when shipped to insure that the owner/end customer of the system initializes the tpm and configures all security passwords. Trusted platform module (tpm, also known as iso/iec 11889) is an international standard for a secure cryptoprocessor, a dedicated microcontroller designed to secure hardware through integrated.
H4f5zm29j1gncm from i.pcmag.com The trusted platform module is disabled by default when shipped to insure that the owner/end customer of the system initializes the tpm and configures all security passwords. 2 trusted platform module (tpm) quick reference guide. Copyright © 2009 intel corporation. Trusted platform module (tpm, also known as iso/iec 11889) is an international standard for a secure cryptoprocessor, a dedicated microcontroller designed to secure hardware through integrated. This chip protects sensitive data and wards off hacking attempts generated through a computer's hardware. Tpm enabled on your motherboard will help against bootkits, rootkits, keystroke harvesting, and many more online attacks against your operating system.
This chip protects sensitive data and wards off hacking attempts generated through a computer's hardware. The trusted platform module is disabled by default when shipped to insure that the owner/end customer of the system initializes the tpm and configures all security passwords. Copyright © 2009 intel corporation. This chip protects sensitive data and wards off hacking attempts generated through a computer's hardware. Tpm enabled on your motherboard will help against bootkits, rootkits, keystroke harvesting, and many more online attacks against your operating system. 2 trusted platform module (tpm) quick reference guide. Trusted platform module (tpm, also known as iso/iec 11889) is an international standard for a secure cryptoprocessor, a dedicated microcontroller designed to secure hardware through integrated.
This chip protects sensitive data and wards off hacking attempts generated through a computer's hardware tpm modul . The trusted platform module is disabled by default when shipped to insure that the owner/end customer of the system initializes the tpm and configures all security passwords. Source: This chip protects sensitive data and wards off hacking attempts generated through a computer's hardware. Tpm enabled on your motherboard will help against bootkits, rootkits, keystroke harvesting, and many more online attacks against your operating system. 2 trusted platform module (tpm) quick reference guide. The trusted platform module is disabled by default when shipped to insure that the owner/end customer of the system initializes the tpm and configures all security passwords. Copyright © 2009 intel corporation.
Source: d2zs7efolu1fdi.cloudfront.net This chip protects sensitive data and wards off hacking attempts generated through a computer's hardware. Trusted platform module (tpm, also known as iso/iec 11889) is an international standard for a secure cryptoprocessor, a dedicated microcontroller designed to secure hardware through integrated. Copyright © 2009 intel corporation. The trusted platform module is disabled by default when shipped to insure that the owner/end customer of the system initializes the tpm and configures all security passwords. 2 trusted platform module (tpm) quick reference guide.
Source: i2.wp.com This chip protects sensitive data and wards off hacking attempts generated through a computer's hardware. Tpm enabled on your motherboard will help against bootkits, rootkits, keystroke harvesting, and many more online attacks against your operating system. 2 trusted platform module (tpm) quick reference guide. Copyright © 2009 intel corporation. The trusted platform module is disabled by default when shipped to insure that the owner/end customer of the system initializes the tpm and configures all security passwords.
Source: data.embeddedcomputing.com Tpm enabled on your motherboard will help against bootkits, rootkits, keystroke harvesting, and many more online attacks against your operating system. The trusted platform module is disabled by default when shipped to insure that the owner/end customer of the system initializes the tpm and configures all security passwords. This chip protects sensitive data and wards off hacking attempts generated through a computer's hardware. Trusted platform module (tpm, also known as iso/iec 11889) is an international standard for a secure cryptoprocessor, a dedicated microcontroller designed to secure hardware through integrated. 2 trusted platform module (tpm) quick reference guide.
Source: i.ebayimg.com This chip protects sensitive data and wards off hacking attempts generated through a computer's hardware. The trusted platform module is disabled by default when shipped to insure that the owner/end customer of the system initializes the tpm and configures all security passwords. Tpm enabled on your motherboard will help against bootkits, rootkits, keystroke harvesting, and many more online attacks against your operating system. 2 trusted platform module (tpm) quick reference guide. Copyright © 2009 intel corporation.
Source: premio.blob.core.windows.net The trusted platform module is disabled by default when shipped to insure that the owner/end customer of the system initializes the tpm and configures all security passwords. Trusted platform module (tpm, also known as iso/iec 11889) is an international standard for a secure cryptoprocessor, a dedicated microcontroller designed to secure hardware through integrated. Tpm enabled on your motherboard will help against bootkits, rootkits, keystroke harvesting, and many more online attacks against your operating system. This chip protects sensitive data and wards off hacking attempts generated through a computer's hardware. Copyright © 2009 intel corporation.
Source: www.cartft.com 2 trusted platform module (tpm) quick reference guide. The trusted platform module is disabled by default when shipped to insure that the owner/end customer of the system initializes the tpm and configures all security passwords. Trusted platform module (tpm, also known as iso/iec 11889) is an international standard for a secure cryptoprocessor, a dedicated microcontroller designed to secure hardware through integrated. This chip protects sensitive data and wards off hacking attempts generated through a computer's hardware. Copyright © 2009 intel corporation.
Source: www.tenforums.com 2 trusted platform module (tpm) quick reference guide. Tpm enabled on your motherboard will help against bootkits, rootkits, keystroke harvesting, and many more online attacks against your operating system. Trusted platform module (tpm, also known as iso/iec 11889) is an international standard for a secure cryptoprocessor, a dedicated microcontroller designed to secure hardware through integrated. The trusted platform module is disabled by default when shipped to insure that the owner/end customer of the system initializes the tpm and configures all security passwords. This chip protects sensitive data and wards off hacking attempts generated through a computer's hardware.
Source: zbook.org The trusted platform module is disabled by default when shipped to insure that the owner/end customer of the system initializes the tpm and configures all security passwords. This chip protects sensitive data and wards off hacking attempts generated through a computer's hardware. 2 trusted platform module (tpm) quick reference guide. Tpm enabled on your motherboard will help against bootkits, rootkits, keystroke harvesting, and many more online attacks against your operating system. Trusted platform module (tpm, also known as iso/iec 11889) is an international standard for a secure cryptoprocessor, a dedicated microcontroller designed to secure hardware through integrated.
Source: premio.blob.core.windows.net This chip protects sensitive data and wards off hacking attempts generated through a computer's hardware.
Source: The trusted platform module is disabled by default when shipped to insure that the owner/end customer of the system initializes the tpm and configures all security passwords.
Source: junipersys.com Trusted platform module (tpm, also known as iso/iec 11889) is an international standard for a secure cryptoprocessor, a dedicated microcontroller designed to secure hardware through integrated.
Source: hacker10.com Tpm enabled on your motherboard will help against bootkits, rootkits, keystroke harvesting, and many more online attacks against your operating system.
Source: www.syslogic.com This chip protects sensitive data and wards off hacking attempts generated through a computer's hardware.
Source: germany.in-24.com Trusted platform module (tpm, also known as iso/iec 11889) is an international standard for a secure cryptoprocessor, a dedicated microcontroller designed to secure hardware through integrated.
Source: www.mpl.ch Trusted platform module (tpm, also known as iso/iec 11889) is an international standard for a secure cryptoprocessor, a dedicated microcontroller designed to secure hardware through integrated.
Source: www.researchgate.net The trusted platform module is disabled by default when shipped to insure that the owner/end customer of the system initializes the tpm and configures all security passwords.
Source: heise.cloudimg.io This chip protects sensitive data and wards off hacking attempts generated through a computer's hardware.
Source: www.proshop.de The trusted platform module is disabled by default when shipped to insure that the owner/end customer of the system initializes the tpm and configures all security passwords.
Source: www.researchgate.net The trusted platform module is disabled by default when shipped to insure that the owner/end customer of the system initializes the tpm and configures all security passwords.
Source: www.usedcomp.de This chip protects sensitive data and wards off hacking attempts generated through a computer's hardware.
Source: i.ebayimg.com The trusted platform module is disabled by default when shipped to insure that the owner/end customer of the system initializes the tpm and configures all security passwords.
Source: developer.pelion.com Tpm enabled on your motherboard will help against bootkits, rootkits, keystroke harvesting, and many more online attacks against your operating system.
Source: cdn-reichelt.de This chip protects sensitive data and wards off hacking attempts generated through a computer's hardware.
Source: www.syslogic.com This chip protects sensitive data and wards off hacking attempts generated through a computer's hardware.
Source: www.vibrant.com Trusted platform module (tpm, also known as iso/iec 11889) is an international standard for a secure cryptoprocessor, a dedicated microcontroller designed to secure hardware through integrated.
Source: images.gutefrage.net This chip protects sensitive data and wards off hacking attempts generated through a computer's hardware.



0 Komentar